
Cimcor Inc. – Technology Integrations
September 25, 2020Why Are Applications Difficult to Secure?
September 25, 2020Automated response with Cisco Stealthwatch
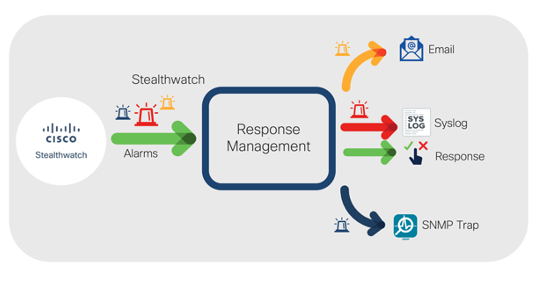
Cisco Stealthwatch provides enterprise-wide visibility by collecting telemetry from all corners of your environment and applying best in class security analytics by leveraging multiple engines including behavioral modeling and machine learning to pinpoint anomalies and detect threats in real-time. Once threats are detected, events and alarms are generated and displayed within the user interface. The system also provides the ability to automatically respond to, or share alarms by using the Response Manager. In release 7.3 of the solution, the Response Management module has been modernized and is now available from the web-based user interface to facilitate data-sharing with third party event gathering and ticketing systems. Additional enhancements include a range of customizable action and rule configurations that offer numerous new ways to share and respond to alarms to improve operational efficiencies by accelerating incident investigation efforts. In this post, I’ll provide an overview of new enhancements to this capability.
Benefits:
- The new modernized Response Management module facilitates data-sharing with third party event gathering and ticketing systems through a range of action options.
- Save time and reduce noise by specifying which alarms are shared with SecureX threat response.
- Automate responses with pre-built workflows through SecureX orchestration capabilities.

The Response Manager uses two main functions:
- Rules: A set of one or multiple nested condition types that define when one or multiple response actions should be triggered.
- Actions: Response actions that are associated with specific rules and are used to perform specific types of actions when triggered.

Alarms generally fall into two categories:
Threat response-related alarms:
- Host: Alarms associated with core and custom detections for hosts or host groups such as C&C alarms, data hoarding alarms, port scan alarms, data exfiltration alarms, etc.
- Host Group Relationship: Alarms associated with relationship policies or network map-related policies such as, high traffic, SYN flood, round rip time, and more.
Stealthwatch appliance management-related alarms:
- Flow Collector System: Alarms associated with the Flow Collector component of the solution such as database alarms, raid alarms, management channel alarms, etc.
- Stealthwatch Management Console (SMC) System: Alarms associated with the SMC component of the solution such as Raid alarms, Cisco Identity Services Engine (ISE) connection and license status alarms.
- Exporter or Interface: Alarms associated with exporters and their interfaces such as interface utilization alarms, Flow Sensor alarms, flow data exporter alarms, and longest duration alarms.
- UDP Director: Alarms associated with the UDP Collector component of the solution such as Raid alarms, management channel alarms, high availability Alarms, etc.

Available types of response actions consist of the following:
- Syslog Message: Allows you to configure your own customized formats based off of alarm variables such as alarm type, source, destination, category, and more for Syslog messages to be sent to third party solutions such as SIEMs and management systems.
- Email: Sends email messages with configurable formats including alarm variables such as alarm type, source, destination, category, and more.
- SNMP Trap: Sends SNMP Traps messages with configurable formats including alarm variables such as alarm type, source, destination, category, etc.
- ISE ANC Policy: Triggers Adaptive Network Control (ANC) policy changes to modify or limit an endpoint’s level of access to the network when Stealthwatch is integrated with ISE.
- Webhook: Uses webhooks exposed by other solutions which could vary from an API call to a web triggered script to enhance data sharing with third-party tools.
- Threat Response Incident: Sends Stealthwatch alarms to SecureX threat response with the ability to specify incident confidence levels and host information.
The combination of rules and actions gives numerous possibilities on how to share or respond to alarms generated from Cisco Stealthwatch. Below is an example of a usage combination that triggers a response for employees connected locally or remotely in case their devices triggers a remote access breach alarm or a botnet infected host alarm. The response actions include isolating the device via ISE, sharing the incident to SecureX threat response and opening up a ticket with webhooks.

The ongoing growth of critical security and network operations continues to increase the need to reduce complexity and automate response capabilities. Cisco Stealthwatch release 7.3.0’s modernized Response Management module helps to cut down on noise by eliminating repetitive tasks, accelerate incident investigations, and streamline remediation operations through its industry leading high fidelity and easy to configure automated response rules and actions.
To learn more about new Automated Response enhancements, check out the Stealthwatch Release 7.3.0 At-a-Glance and the Release Notes.
Don’t have Stealthwatch? Learn more by visiting https://www.cisco.com/go/stealthwatch or try the solution out for yourself today with a free visibility assessment.
The post Automated response with Cisco Stealthwatch appeared first on Cisco Blogs.

