How Adversaries Use Politics for Compromise
November 5, 2019
Relentless Breach Defense Endpoint Protection Platform + Endpoint Detection and Response
November 6, 2019Establishing Device Trust to Secure the Workforce
Challenges of Protecting Endpoints
With an estimated 70% of breaches starting on endpoints – laptops, workstations, servers, and mobile devices – organizations need visibility into the devices connecting to applications both on the network and in the cloud. Organizations need the ability to establish trust in the devices connecting to resources containing sensitive information.
Curious how you can determine if you can trust the endpoints that are connecting to your business resources? Ask yourself a few quick questions:
- Are you able to automatically notify users of out-of-date software to reduce your help desk tickets or block devices that have been compromised? Or automatically quarantine malicious files from infecting your entire network?
- Can you enforce endpoint controls for risky devices or corporate-owned devices? What about contractor devices or external third parties connecting to your network?
- Can you enforce access policies based on the application risk or whether the device is a known healthy device that meets security guidelines?
Establishing Trust in Endpoints
In order to effectively establish trust in user devices, organizations should have device-based policies in place to prevent access by any risky or unknown devices. By validating the device is both healthy and meets security policies, you can ensure they’re trustworthy – key components of the Cisco Zero Trust security approach for the workforce.
Cisco implements zero trust with a three-step methodology across the workforce, workloads and workplace by:
- Establishing trust of a user, device, application, etc. – before granting access or allowing connections or communications.
- Enforcing trust-based policies with granular controls based on changing context – such as the security posture of devices and the behavior of applications
- Continuously verifying trust by monitoring for risky devices, policy noncompliance, behavior deviations and software vulnerabilities
With Duo and Cisco® Advanced Malware Protection (AMP) for Endpoints, organizations have the tools in place to effectively establish trust in users’ devices connecting to protected applications. The ability to prevent, detect and respond are key elements when considering device trust in a zero-trust security approach for the workforce.
Trust Through Protection and Detection
Establishing trust extends beyond managing the status of the device to include inspecting the device and controlling access based on risk evaluations to ensure only devices that are healthy and meet your security controls are able to gain access to your corporate systems. With Duo Trusted Endpoints, you can enforce controls and policies to keep risky endpoints from accessing your applications. This includes devices that are unmanaged; don’t meet OS requirements; status of enabled security features (configured or disabled); full disk encryption.
AMP for Endpoints offers endpoint protection, advanced endpoint detection and response capabilities and a holistic view of your endpoints, regardless of operating system. AMP continuously monitors and analyzes all file and process activity within your network to find and automatically block threats that other solutions miss. It has more than 15 built-in protection and detection mechanisms to prevent threats from compromising your business. With a few clicks in AMP’s browser-based management console, the file can be blocked from running on all endpoints. AMP knows every other endpoint the file has reached, so it can quarantine the file for all users.
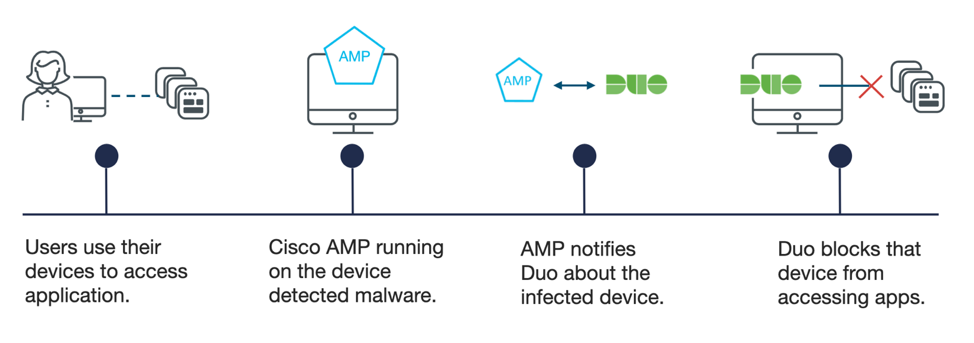
Available Soon – Integration between Duo Security and AMP for Endpoints
Adding AMP for Endpoints as a Trusted Endpoint in Duo provides the ability to protect applications from devices that have been flagged by AMP as an infected endpoint containing malware. This prevents access to any application that contains sensitive data reducing the risk of data loss.
Duo’s access policies will allow admins to entirely block access to devices flagged by AMP without blocking the user entirely, permitting them to access applications from an alternate device to ensure continued productivity.
The automatic isolation and blocking of compromised devices provides organizations the ability to quickly remediate potential threats, reducing their risk surface without completely interrupting user productivity.
Duo and AMP provide organizations with comprehensive tools to prevent, detect and respond to potential threats from endpoint devices, helping to establish trust in those devices.
Learn more about Cisco Zero Trust, and get started with a free trial of Duo and Cisco AMP for Endpoints to start establishing trust in your endpoints today.


