Scalable Security with Cisco Secure Firewall Cloud Native
May 26, 2021
To become a digital-first nation, there needs to be a cloud-first mindset
May 28, 2021Going on-premise with SecureX orchestration remote
Cisco SecureX has been enabling customers to build more secure, integrated infrastructure for over a year now. Leveraging both Cisco and third-party integrations, you can centralize visibility and aggregate intelligence while conducting incident investigation and response. SecureX orchestration allows you to take these integrations to the next level by creating custom workflows that enable your products to interact with each other in entirely new ways. However, since the SecureX platform is cloud-based, integration with on-premise resources has proven to be a challenge. Many of our customers have expressed interest in these types of integrations and now it’s possible!
SecureX orchestration remote
With SecureX orchestration remote, you can start to integrate on-premise resources into your orchestration workflows. The remote is a virtual appliance that you run behind your firewall to broker requests from the cloud. Once it’s up and running, SecureX orchestration can send requests to your on-premise resources through the remote. You can even have multiple remotes if you want them inside different networks or data centers. Cisco provides the remote as an easy to deploy OVA for VMware ESXi version 5.5 (or newer) and the appliance’s compute requirements are minimal. We recommend 2 vCPU, 2 GB of RAM, and 30 GB of disk. The remote also requires outbound connectivity to the internet over TCPS port 8883 to the SecureX cloud.
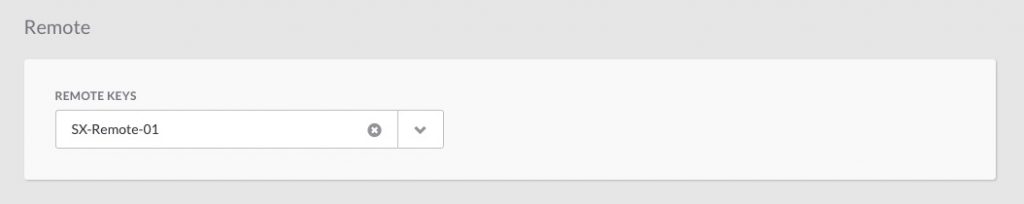
Configuring your orchestration targets to use a remote is as simple as selecting the remote you want to use from a drop down list when creating or modifying a target:

On-premise use cases
Now that we have the ability to integrate with on-premise resources, let’s talk about some new orchestration use cases. Alongside the release of SecureX orchestration remote, we’re releasing our first workflows and atomic actions for two on-premise products: Cisco Secure Firewall and Cisco Identity Services Engine (ISE). These workflows include:
- 0027 – ISE – Quarantine Endpoint
- 0028 – ISE – UnQuarantine Endpoint
- 0029 – ISE – Add Endpoint to Identity Group
- 0030 – ISE – Remove Endpoint from Identity Group
- 0031 – Secure Firewall – Microsoft Online Dynamic Object Update
Spotlight: ISE – Quarantine endpoint
Spotlight: Secure Firewall – Microsoft Online Dynamic Object update
Resources
Ready to get started with SecureX orchestration remote? The best place to start is our SecureX orchestration remote documentation. In these docs, you’ll learn how to set up a remote and how you can use it in your workflows.



