
Global BIM Policies and Standards Important for Public Projects
March 10, 2021
A culture of innovation fuels business resilience and economic recovery in Malaysia
March 11, 2021How to Balance IT Stability and Strong Security
Remember the old days of deploying Anti-Virus (AV) across your organization? Most often, it was a “set it and forget it” approach. It worked back then. Until it didn’t.
This leaves us with a perplexing dichotomy. On the one hand, the mindset of the old AV days still persists, where many companies are reluctant to update, upgrade, or even touch their existing security technology. On the other hand, we found in our recent 2021 Security Outcomes Study that most practitioners believe a technical refresh is the most prudent approach to staying ahead of existing and emerging threats.
So where is the problem? What is it that causes organizations to resist upgrading?
Instability as a Source of Insecurity
The problem is one of stability. After all the configurations have been tweaked to make a deployed product behave as a finely tuned engine, there is nothing more uncertain than having a vendor announce a new product that has the potential to disrupt your harmonious tech orchestration. To state it more bluntly, people have been burned too many times with the promise of the latest and greatest software that ultimately interrupts their workflow and, in some cases, entirely halts production.
This is the classic struggle between operations and security; they do not always line up. Everything might be flowing smoothly, but when an exploit emerges that an attacker could use to compromise the organization, the security team is viewed by the organization as overly paranoid if they want to make changes, threatening the stability of a perfectly functioning environment. In other instances, the security team may not even have the time to stay on top of necessary updates, leading to “upgrade resistance” even among the security ranks.
Why Is Stability Threatened When a New Product Is Introduced?
According to our Security Outcomes Study, it would seem that the inability to retain skilled security professionals may be part of the problem. Another factor is that even with a staff of skilled professionals, they are often stretched beyond their capabilities and are expected to do too many tasks in the course of a normal workday. Unfortunately, short staffing and an overworked security team can lead to a lack of testing, which can create issues when it comes to effectively implementing software updates.
How to Ensure Success
Proper training
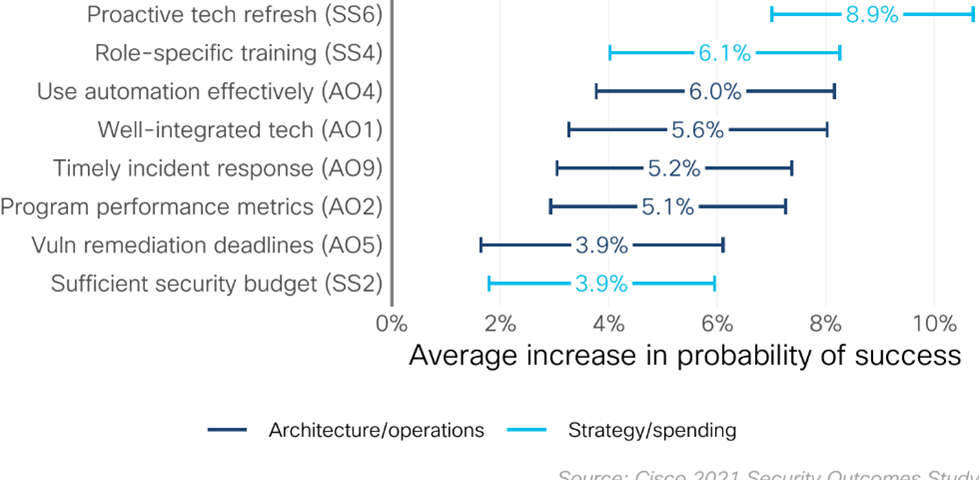
When we think about the tools needed to succeed, one of the best tools for any staff is training. If you offer training to the staff, you end up not only with a stronger, more skilled team but also a team that feels valued and appreciated. As shown below, role-specific training is one of the top success factors that can help a security team keep up with business demands.

I am often reminded of a joke that I heard where a manager asks, “What happens if we spend money on training and the staff then leaves?” To which the other person responds, “What happens if you don’t train them and they stay?”
It is all about instilling confidence in the team and empowering them to make the correct choices when it comes to what’s best for an organization’s overall infrastructure. For example, testing prior to deployment is an absolute necessity towards the success of any project.
Reliable vendors
Another key to ensuring success is to work with reliable and trustworthy vendors. The vendor relationship is important from a technology standpoint as well as a business standpoint.
How can you combat the fear of new security technology in an organization? You can do so by imparting stability into project plans, which can be achieved by elevating your staff’s qualifications and by working with reputable vendors. As shown below, properly managing vendor security is one of the top success factors for creating a strong security culture within an organization.

Automated, integrated technology
Last but certainly not least, technology itself can help with maintaining a stable and secure environment, while not letting software get out-of-date. In addition to protecting an organization’s infrastructure, security technology should ideally empower teams as well. It should provide security professionals with a boost, not a burden.
Seek out security technology that is streamlined, integrated, and automated. Unfortunately, the culture of procuring a new point product for every new security threat has left us with crushing complexity in many cases. Vendors today must simplify their security offerings by making them work together to reduce the manual processes that often slow down security teams.
By lessening the tedious, time-consuming tasks that stand in the way of fast, effective security, an integrated, automated tool set can help security teams more confidently stay on top of technology updates – and implement them more safely and securely. In time, this confidence can extend over to other parts of the organization and lessen overall resistance to change. After all, you cannot properly secure an organization with stagnant technology.
How Cisco can help
Cisco has been on a mission for several years to simplify and streamline its security capabilities. With the launch of Cisco SecureX, we introduced an integrated platform that incorporates greater visibility, efficiency, and automation into security processes. It brings together our entire Cisco Secure portfolio, as well as many third-party technologies, to streamline and strengthen operations not just for security teams, but for IT and networking groups as well.
With SecureX, these various teams can more easily collaborate – viewing and responding to the same data in the same place – to more quickly and effectively identify and troubleshoot potential issues. Additionally, since SecureX is delivered via the cloud, it is easy to add or update security capabilities as needed, further lessening the burden of proactive tech refreshes.
While there are many steps that can be taken to strengthen security, our Security Outcomes Study suggests that proactive tech refreshes, training, strong vendor relationships, and integration and automation can all go a long way.
Learn how Cisco Secure Products and Solutions can help you balance
IT stability and security for a stronger, more harmonious infrastructure.

