
Get a Stable Internet Connection for Gaming
April 10, 2020
Alternative ways for security professionals and IT to achieve modern security controls in today’s unique remote work scenarios
April 11, 2020Promising Results for Post-Quantum Certificates in TLS 1.3
The Challenge
Quantum Computers could threaten the security of TLS key exchange and authentication. To assess the performance of post-quantum certificates TLS 1.3, we evaluated NIST Round 2 signature algorithms and concluded that two of them offer acceptable speeds. We also analyzed other implications of post-quantum certs in TLS. More details in https://ia.cr/2020/071
We all know by now that the potential development of large-scale quantum computers has raised concerns among IT and security research professionals due to their ability to break public key cryptography. All currently used public key algorithms would be deemed insecure in a post-quantum (PQ) setting. In response, the National Institute of Standards and Technology (NIST) has initiated a process to standardize quantum-resistant crypto algorithms, focusing primarily on their security guarantees.
The Tests
The industry has been evaluating some of these algorithms for use in encryption protocols like TLS and IKEv2/IPsec. Cloudflare, Google, and AWS have been looking into PQ TLS key exchange. At Cisco, we focused on PQ authentication/certificates in TLS 1.3. We briefly discussed some of our early results in a recent blog post and detailed them in our paper presented at ETSI/IQC Quantum Safe Cryptography Workshop 2019.
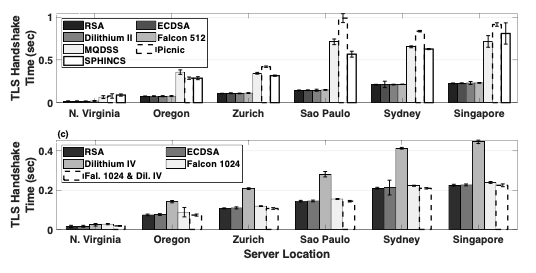
A couple of months ago, we presented all of our results in our paper at NDSS 2020 in San Diego. The paper presented a detailed performance evaluation of the NIST signature algorithm candidates and investigated the imposed latency on TLS 1.3 connection establishment under realistic network conditions. In other words, we deployed servers all over the world. We proved that at least two candidate PQ signature algorithms perform similarly to RSA/ECDSA certificates, as shown in the figure below.

We also investigated PQ signature impact on TLS session throughput and analyzed the trade-off between lengthy PQ signatures and computationally heavy PQ cryptographic operations.
The Results
Our results demonstrated that the adoption of at least two PQ signature algorithms would be viable with little additional overhead over current signature algorithms. Also, we argued that many NIST PQ candidates could effectively be used for less time-sensitive applications, and discussed in depth the integration of PQ authentication in encrypted tunneling protocols. Finally, we evaluated and proposed the combination of different PQ signature algorithms across the same certificate chain in TLS. The results showed a reduction of the TLS handshake time and a significant increase of a server’s TLS tunnel connection rate over using a single PQ signature scheme.
For more details on the impact of PQ certificates on TLS, refer to our NDSS 2020 paper.
For additional resources, visit trust.cisco.com
The post Promising Results for Post-Quantum Certificates in TLS 1.3 appeared first on Cisco Blogs.

