Threat Protection: The REvil Ransomware
August 11, 2021
Black Hat USA 2021 Network Operations Center
August 12, 2021Recapping Cisco Secure at Black Hat USA 2021
There is always excitement in the air throughout the Security community at this time of year; usually we excitedly approach “Hacker Summer Camp.” This year, like last, was a little different from what we have become used to over the last 24 years. Cisco Security was honored to be a sponsor of the 24th Black Hat USA 2021 Conference – the internationally recognized cybersecurity event series providing the security community with the latest cutting-edge research, developments and training. For a complete list of Cisco-sponsored sessions, demos and resources, visit the Cisco Secure Black Hat page.
This year’s hybrid event included cybersecurity experts delivering insightful presentations addressing some of today’s top industry challenges. In case you missed them, below is a brief recap of some of the Cisco sessions, including a fight that almost broke out between the Incident Response (IR) team represented by Matt Olney, Talos’ Intel Director, and Wendy Nather, Head of Advisory CISOs. Read on for details…
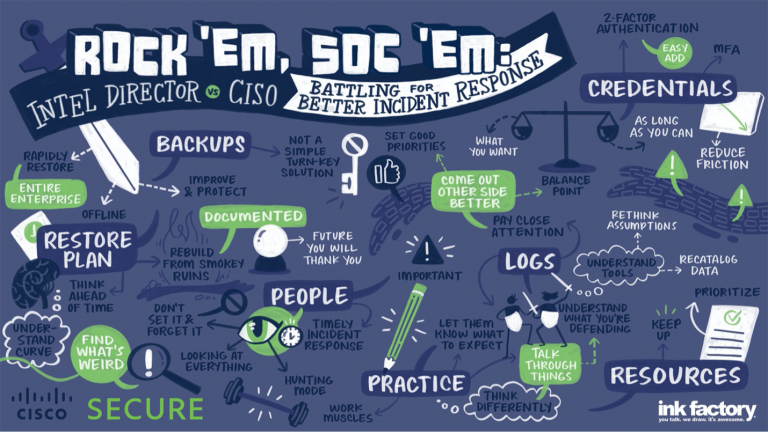
Black Hat Featured Session: Rock ‘Em, SOC ‘Em – Intel Director vs. CISO Battling for Better Incident Response
Effectively responding to unexpected security incidents is a mighty task that requires expertise and loads of skill. In this session, Matt and Wendy gave their hot takes on five critical points related to responding to and preventing pesky cyber breaches and incidents.
Backups… Let’s Get This Out of the Way
Wendy and Matt chatted about the challenges and importance of backing up data. Wendy opened the conversations by addressing how backing up data is primarily outsourced to third parties’ organizations by businesses. A challenge with outsourcing backup responsibilities is that companies often have no say in how often or the level at which third parties back up their information. Most importantly, if backups are online, they have a higher chance of being susceptible to malware and other cyber-attacks.
Matt responded stating that backups are not a simple turnkey solution; serious questions must be asked before implementation. The twenty-first century dilemma that executives now face is deciding if it’s quicker to pay ransoms when their organizations get hacked to decrypt their systems or restore their systems via backups. Wendy ended by reminding the audience of the importance of a restoration plan in the event of an attack and testing backups with the third party to see how effective they are.
“With ransomware being as big as it is right now, one of the first answers that everyone goes to is backups.” -Wendy Nather
Don’t Set It and Forget It
Matt kicked it off by calling out CISO’s for buying and installing new security systems in response to cyber incidents. An issue with this response is linked to the configurations and lack of upkeep of new security systems once installed. According to Matt, people often had the right tools but were not configured correctly or were not effectively monitored to prevent future attacks. Wendy argued that often members of the security industry have a habit of setting up security systems and never checking on them again due to time and responsibility constraints. Wendy mentioned the importance of checking on security systems that do not seem like red flags. When it comes to cybersecurity, one can never be too careful, especially in our digital age.
“It’s easy to forget about a particular security control if there’s nothing wrong with it – if it doesn’t make noise.” -Wendy Nather
Practice, Practice, Practice
Practice makes perfect, especially in the cybersecurity space. Matt emphasized the importance of practicing for incident responses ahead. Whether a company has a playbook or robust incident response plans, Matt assured the audience that running through different incident scenarios will prove beneficial in the future. Wendy pushed back on Matt’s argument by talking about the logistics. Wendy highlighted the price of planning and executing incident scenarios can cost business and questions its feasibility. However, Wendy later acknowledged that some of the most mature organizations she has talked to practice incident response every week. Planning for cyber-attacks is expensive, so it is up to businesses to weigh its risks and rewards.
“Every hour you have spent in the previous years prepping for [an attack] makes that day less awful.” -Matt Olney
Logs. LOGS For the LOVE of LOGS
Constantly logging in the security industry is incredibly important, especially for Intel Directors like Matt. Matt argued that the lack of logging in data hurts incident response teams the most. It is difficult for incident response teams to help businesses after security breaches if specific data from security systems are not recorded. To Matt’s point, Wendy questioned if logging at the level that Matt suggests is realistic for an organization. Wendy explained how expensive logging is and how it can make responding to security breaches more complicated at times. Matt agreed that one cannot log everything; an effective logging balance must be achieved within a company’s security unit.
“You can’t log everything forever, but you need that kind of balance point between getting what you need for as long as you can.” -Matt Olney
Compromised Credentials: THE Most Observed Initial Access Vector
Multi-factor Authentication (MFA) has proven to be a godsend to the cyber security community and both Matt and Wendy raved about the technology during their chat. Matt mentioned the effectiveness of multifactor authentication, calling it a relatively simple addition to a business security that can render multiple hacking methods less potent. Meanwhile, Wendy highlighted the importance of choosing a seamless MFA experience that users can enjoy and ultimately won’t mind using. In addition, Matt personally prefers the newer MFA system than the age-old firewall system. Overall, both Matt and Wendy are on the same page regarding the effectiveness of an MFA system.
“There is nothing that is not widely deployed already that has the sort of bite and scope that MFA has.” -Matt Olney

Want to hear from more Cisco experts? Check out these other Black Hat sessions exploring ransomware, threat intelligence and more.
Resilient Incident Response: Responding to Ransomware Attacks
Watch Brad Garnett, GM of Incident Response at Cisco Talos Intelligence Group, share practical incident response strategies that every CISO and business leader faces with a hybrid workforce, including insights from the frontlines in the fight against ransomware and evolving adversaries.
Recent Trends in Ransomware
Watch as Cisco Talos Research Engineer Edmund Brumaghin dissects the key changes in recent ransomware attacks and how organizations can proactively reduce the risk associated with them.
Getting from Intelligence to Incident Response
Learn more about Cisco Talos and Cisco Talos Incident Response (CTIR) in this presentation by Liz Waddell, Incident Commander at CTIR, to see how we leverage our unmatched visibility, threat intelligence and collective response time to help protect customers.
A Lighthouse in the Darkness: Let Your Defense Shine
Finally, I was joined by Christopher Marshall, Director of Cisco Talos Threat Detection and Response, to discuss how defenders are planning and preparing for today’s sophisticated threat landscape and the tremendous value of trusted intelligence in protecting you from both known and emerging threats.
Cisco Talos is one of the largest commercial threat intelligence teams in the world, comprised of world-class researchers, analysts and engineers. Talos defends Cisco customers against known and emerging threats, discovers new vulnerabilities in common software and interdicts threats in the wild before they can further harm the internet at large. To learn more about Cisco Talos, visit talosintelligence.com. You can also subscribe to Talos’ Threat Source newsletter, read the Talos blog, listen to our popular Beers with Talos podcast and follow us on Twitter at @talossecurity.
We’d love to hear what you think. Ask a Question, Comment Below, and Stay Connected with Cisco Secure on social!
Cisco Secure Social Channels
Instagram
Facebook
Twitter
LinkedIn

