
Threat Roundup for March 19 to March 26
March 28, 2021
Cisco’s Vision for SASE and a Brand New Offer to Kickstart Your Journey
March 30, 2021SASE, ZTNA and XDR market trends must work together for simplified security
Secure Access Service Edge (SASE), Zero Trust Network Access (ZTNA), and Extended Detection and Response (XDR) are market trends that had started well before the year 2020. But last year they were both accelerated and catalyzed at warp speed to fundamentally overhaul the security industry. Some observers say as much as a decade’s worth of digital transformation occurred across the IT industry since RSA Conference 2020 to keep businesses resilient throughout the pandemic. And the team at 451 Research shared their thoughts on how these trends are expected to reshape security in 2021 and beyond – click here to read it now.
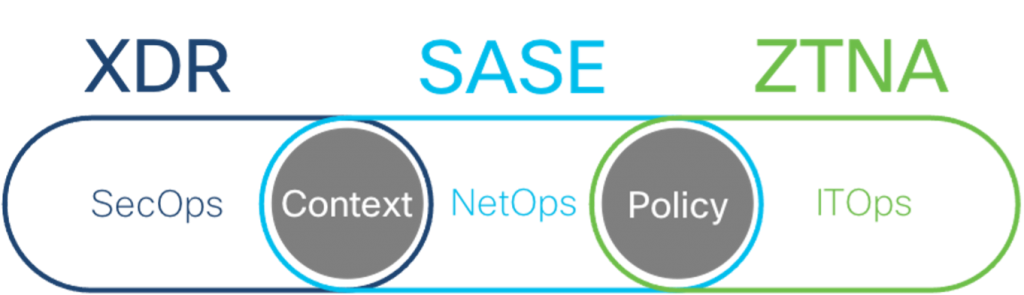
What is the relationship between ZTNA, SASE, and XDR? Is one more relevant as you begin preparing for an increasingly distributed environment where your perimeter no longer belongs in a box? In short, they are not mutually exclusive. These three trends are reshaping security (click each link to learn more)
- The SASE trend is rearchitecting many disparate networking and network security functions into one consolidated service.
- The ZTNA trend is building continuous trust verification by enforcing connectivity policies based on the actual users, devices, and services, not network locations.
- The XDR trend is integrating multiple security control points and applying analytics and automation to make detection and response faster and easier.

Harness the intersection points
Before diving into the specifics, it is critical to understand how these trends can improve your existing security and create combined value at the intersection points. The increasing consumerization of IT and the growing distributed network of users who access business-critical applications are posing a real and serious challenge for security teams. Consequently, traditional network approaches do not satisfy the complex need to balance security with access. Access control itself has evolved considerably with endpoints leaving the building and device proliferation adding to the ITOps woes. Do you have the right integration with your control points, are you built to verify authorization, mediate policy-compliant access and protect against unauthorized access attempts? Just keep those answers in your head, and now reconsider it against the evolving threat landscape with active adversaries who are well-funded and endlessly patient. In this context, ZTNA and SASE work together by converging a no-trust access strategy with an architecture that represents the evolving IT environment. XDR builds on this no-trust strategy to help deliver detection and response that can scale quickly.
“It’s not about getting rid of the perimeter – but rather tightening security on the inside. The new perimeter is less about the edge of the network, and now more about any place you make an access control decision.”
Wendy Nather, Head of Advisory CISOs, Cisco Duo, Summarized from Zero Trust: Going Beyond the Perimeter
Despite an increase in security investments, most organizations are experiencing longer threat dwell times within their security ecosystem — 280 days on average1. Why is that? The industry has designed products, often marketed as platforms, that prioritize protecting one threat vector, creating solutions that don’t easily integrate. The telemetry data logged by each security tool often is analyzed in isolation — often lacking the fidelity to detect more subtle and hidden attacks. Then, the alerts generated are decided upon in isolation — often concluding too little malicious intent or risk exposure for teams to act quickly or at all due to limited resources. And when teams do act, the response happens one control point at a time without efficient coordination — wasting time and often failing to completely defend against the breach. You need a platform that can meet your evolving enterprise needs to connect trusted users to the right applications on the network fast and do so securely. You need a solution that is continuously nourished with contextual insights from your network to make access control decisions. But the real question is: How do you continually verify trust for both users and devices at scale when massive data and device proliferation is part of today’s reality? And how do you continuously assess the health of your endpoints/systems and the impact of threats on your environment?
These trends must work together, not in isolation:
- SASE and ZTNA intersect as NetOps and ITOps establish a common identity- and context-based policy across all digital devices– including those that are unmanaged and in the cloud.
- XDR and SASE (and by extension, ZTNA) intersect as SecOps and NetOps/ITOps continuously assess risk/trust-based not just on context from network analytics, but also endpoint security, email security, and beyond.
- SASE, ZTNA, and XDR individually promise to simplify your operations, yet you will inevitably adopt at least two if not all three approaches over the next few years. As you plan how to keep your business resilient today and into the future, we recommend evaluating each of your security vendors’ platforms for the breadth and depth of integration to simplify security across all three.
What approach is right for you? Take the Cisco SecureX litmus test
As the largest enterprise cybersecurity company in the world, Cisco leads the way with solutions that are driving the industry in SASE, XDR, and zero trust. Integrating it all is Cisco SecureX, our security platform that provides simplicity, visibility, and efficiency across your security environment. With Secure access service edge (SASE), we combine network and security functionality in a single, cloud-native service to help secure access wherever users and applications reside. Technologies that play in the SASE space build context about network activity or serve as policy enforcement points to deliver insights needed access decisions. This includes the Zero trust approach that balances security and usability while you protect against threats to users, networks, and applications. You also need effective security and threat prevention as you shift your on-prem security stack to the cloud and set your team up for success with SASE, ZTNA and XDR. Moreover, we can boost operational productivity using a cloud-native platform with analytics and automation built in to deliver Extended detection and response (XDR) across your environment. Our platform approach includes the most comprehensive XDR capabilities to intelligently detect and respond confidently. From initial access to impact and the mitigations to execution, lateral movement, or exfiltration in between. Cisco can connect many layers of machine learning-enhanced analytics across multiple data sources to accurately identify malicious intent and risk exposure. Once you have unified your multiple security functions in the cloud and extended control beyond the perimeter, you move to control and focus on security and policy enforcements across your network and users. That’s why integrated networking and security services are so important, so you can get out of the business of managing piecemeal products from multiple providers.
“What does the shift toward IT as a service mean for network threat detection, and where can organizations regain telemetry that could be lost through such moves? Might the contributing technologies of SASE have a role to play in the evolution of XDR beyond the traditional enterprise?”
451 Research Team Scott Crawford, Garrett Bekker, Fernando Montenegro, Aaron Sherrill, Eric Hanselman
We realize there’s no one-size-fits-all approach. Implementing an architecture that aligns with these megatrends is a multi-step journey that will be different for each organization, but the time to start is now. To achieve SASE, ZTNA, and XDR with multiple security outcomes, Cisco Secure customers are entitled to our cloud-native, built-in platform — Cisco SecureX. Since 2018, Cisco has reduced this complexity by investing in a platform approach across the industry’s broadest security portfolio, not just one or two-point products. Cisco’s vision for a security platform is built from a simple idea -security solutions should act as a team, learning from each other, listening, and responding as a coordinated unit. Our platform, Cisco SecureX, connects the breadth of Cisco’s integrated security and networking portfolio and your entire security infrastructure for a consistent experience that unifies visibility, enables automation, and strengthens your security across your network, endpoints, cloud, and applications. We’re committed to creating a platform that delivers a better security experience at every point in your network. You can connect your existing security tools–Cisco or third-party—to block, detect, investigate, and respond to threats across your entire environment with true turnkey interoperability. What makes our approach simpler is that we are natively integrating more and more of our detection and response capabilities from each product into others for a simplified experience — rather than always forcing teams to pivot into yet another security tool.
Do you know of any other cloud-native platform that can simplify the security experience for ITOps and NetOps in addition to SecOps? SecureX isn’t another technology layer — rather it maximizes the potential of your existing security solutions. You can start small with a single product and grow as your needs dictate.
To learn more about these trends, check out 451 Research’s report. And to learn about the broadest, most integrated security platform that simplifies your experience across all three trends, visit cisco.com/go/securex.
- Source: Ponemon Institute research featured in IBM’s Cost of a Data Breach Report 2020

