
How Exploit Intel Makes You Less Vulnerable
February 4, 2022
NetApp Hosts Third Quarter of Fiscal Year 2022 Financial Results Webcast
February 5, 2022The White House Memo on Adopting a Zero Trust Architecture: Top Four Tips
On the heels of President Biden’s Executive Order on Cybersecurity (EO 14028), the Office of Management and Budget (OMB) has released a memorandum addressing the heads of executive departments and agencies that “sets forth a Federal zero trust architecture (ZTA) strategy.” My good friend and fellow Advisory CISO Helen Patton has done a great summary of the memo in a previous blog.
The biggest news is the deadline: The memo requires agencies to meet “specific cybersecurity standards and objectives by the end of Fiscal Year (FY) 2024 in order to reinforce the Government’s defenses against increasingly sophisticated and persistent threat campaigns.” More urgently, within 30 days of the publication of the memo, agencies need “to designate and identify a zero-trust strategy implementation lead for their organization.” And within 60 days, agencies need to submit an implementation plan and a budget estimate.
Whenever a deadline is announced, teams can lose sight of the bigger picture in their rush to become compliant. So, we’ve put together the following recommendations to assist IT and IT security practitioners in making the most of this new mandate.
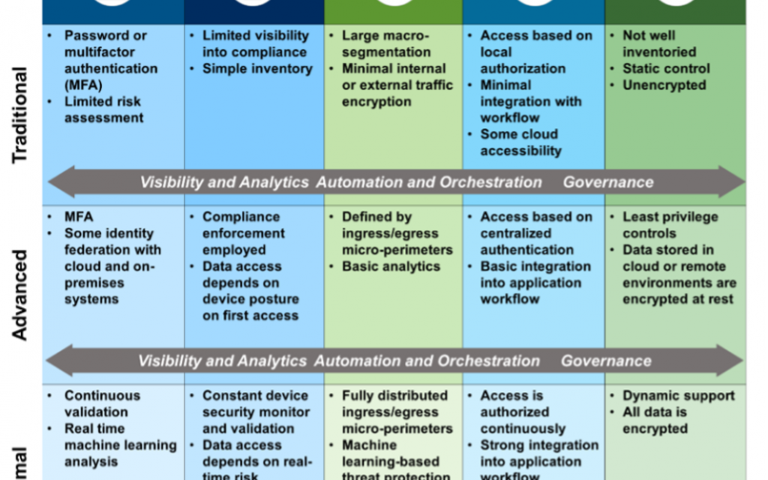
1. Plan, do not panic. For even simple IT initiatives — and deploying a zero-trust architecture is not simple — a plan is always the first step to meeting the deadline. Keep in mind that not all agencies are starting at the same point in terms of security posture or risk exposure. For this reason, the CISA guidance uses a maturity model for zero-trust architecture.

In other words, one size does not fit all. As part of the planning exercise, agencies can assess where they are for each control category in terms of “Traditional”, “Advanced” or “Optimal” (as seen in the above diagram). Here are some questions to tailor our efforts:
- Identities – Is multi-factor authentication (MFA) in place for some but not all applications (e.g., in the cloud but not on-premises)? Is it in place for some but not all of the workforce (e.g., employees but not contractors)? Is the validation done on a continuous basis or only at the point of access?
- Devices – Are the devices authenticated and managed? To what degree can we tie access polices to a device’s security posture? (e.g., is device access dependent on device posture at first access as well as changing risk?)
- Network / Environment – How granular are the network segmentation policies (e.g., tightly scoped resource networks or large flat networks)? Is the policy applied on a continuous basis or only at the point of access?
- Application Workload – How and where are workload policies enforced? Is access policy based on local authorization, centralized authorization, and is it authorized continuously?
- Data – How and where is data stored? Where is encryption used to protect data at rest? Do the policies above provide least trust and least privilege when the workforce is accessing our data?
Provide guidance internally to foster understanding and gain buy-in. This can take the form of a position paper, initial guidelines, and the overall project plan. As work progresses, provide policy and standards language to institute the zero-trust principles and architecture within the agency.
Bottom line: Take your time. After all, OMB recognizes the enormity of the effort. “Transitioning to a zero-trust architecture will not be a quick or easy task for an enterprise as complex and technologically diverse as the Federal Government.”
2. Focus on coverage first: People, devices, apps – in that order. Starting with securing user access via multi-factor authentication (MFA) is consistent with the updated guidance. Per the memo, “this strategy places significant emphasis on stronger enterprise identity and access controls, including multi-factor authentication (MFA). Without secure, enterprise-managed identity systems, adversaries can take over user accounts and gain a foothold in an agency to steal data or launch attacks.” Additionally, the memo directs agencies to consolidate identity systems to more easily apply protections and analytics.
Keep in mind, not all MFA is equal. Agencies are well-served to prioritize solutions that deliver a frictionless user experience, and hence encourage good behavior. At the same time, these solutions should support modern and more secure authentication like passwordless.
Assessing device trust – authenticating a device and using device posture in access decisions – is essential for implementing a zero-trust architecture. After all, a single insecure or unpatched device can allow an attacker to obtain access and maintain persistence – a key step in escalating their attacks.
That’s why enabling users to remediate their own devices before they gain access to an application provides both a better user experience as well as improved security.
The future is here. Users – even in the public sector — no longer login to networks, they log into apps. And notably, the OMB has recommended that every application be treated as if it’s internet-accessible from a security perspective. Plan to increase the coverage of people, their devices, and our applications to make the strongest policy decisions.
3. Increase signal strength and deepen policy enforcement. One of the tenets of zero trust is that “access to resources is determined by policy, including the observable state of user identity and the requesting system, and may include other behavioral attributes.” (NIST 800-207) Early in the plan, assessing “state” may be done by strong user authentication and device posture alone. The memo states that “authorization systems should work to incorporate at least one device-level signal alongside identity information about the authenticated user when regulating access to enterprise resources.” But as we proceed, we should add additional signals of trust to improve the telemetry and accuracy of our policy decisions.Agencies should first become comfortable with policy and increase use of the data points and signals of trust available to us from our tooling. Then, as we gain momentum from early wins on inventory and device control, and as we increase the use of our investments through enabling more of the policy set, we can look to further build trust in our security through behavioral analysis and anomaly detection.
4. Leverage zero-trust frameworks, lessons learned, and other guidance. Within 30 days of the memo’s publication (by February 26, 2022), agencies need to designate and identify a zero-trust strategy implementation lead for the organization. These designated representatives will engage in a government-wide effort to plan and implement zero-trust controls within each organization. While each of these leaders bring unique perspectives and priorities, using common reference architectures and sharing lessons learned can keep teams aligned and focused.
To help with this effort, Cisco offers free, virtual workshops to better understand how zero-trust principles work in practice. Workshop attendees will hear tips directly from former CISOs like me, engage in hands-on activities, and walk away with the tools they need to develop an action plan.
We’d love to hear what you think. Ask a Question, Comment Below, and Stay Connected with Cisco Secure on social!
Cisco Secure Social Channels

