
A Platform Approach + Precise Analytics = Better Equation
February 27, 2020New Research Paper: Prevalence and Impact of Low-Entropy Packing Schemes in the Malware Ecosystem
February 27, 2020Threat hunting doesn’t have to be difficult—Taking a proactive position with your cybersecurity
Your Endpoint Protection Platform (EPP) is up to date with the latest version. Your Endpoint Detection and Response (EDR) technology has all of the latest framework rules and automaton in place. Vulnerabilities and patches for hardware and software are all covered. Your Defense in Depth strategy appears to be keeping your organization secure. But, and there is always a “but”, some adversarial techniques are difficult to DETECT even on a good day. Exfiltration can be quite difficult to detect even if you are looking for it.
As advanced threats continue to proliferate throughout an organizations’ IT resources, threat hunting as a practice has appeared. For an elite security organization, threat hunting takes a more proactive stance to threat detection. Threat hunting was a natural, security progression saved for the most mature environments where skilled personnel leverage knowledge and tools to formulate and investigate hypotheses relating to their organization’s security across the landscape. Now with technology advancements and automation, threat hunting has now become within reach for every organization.
Threat hunting is an analyst-centric process that enables organizations to uncover hidden, advanced threats, missed by automated preventative and detective controls.
Security professionals are beginning to discover threat hunting practices to advance their detection and response monitoring. Threat hunting requires a highly skilled person as well as wide-ranging data forensics and live response across the IT environment. There are only a handful of companies in verticals such as financial services, high-tech manufacturing, and defense that can claim to have advanced threat hunting teams that deliver results.
Today’s threat actors are well-organized, highly intelligent, motivated and focused on their targets. These adversaries could be lurking on your network or threating to break into it, using increasingly sophisticated methods to reach their goal. In addition, the attacks can come from many different threat surfaces to exploit the many vulnerabilities that may be present across an organizations’ network and people. Worst of all, organizations do not know by whom, when, where or how a well-planned attack will occur. Today’s rule-based defenses and solutions have limitations, even advanced detection mechanisms struggle to anticipate how attack vectors will evolve. To mitigate threats more proactively, organizations must move quicker than the speed of the threat. The easiest way to put it, when the existing rules are undermined, it is time to start threat hunting.

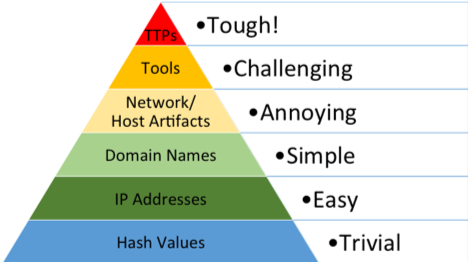
Threat Hunting also allows security teams to address the top most tiers of the Pyramid of Pain, making more difficult for adversaries to impact environments. At the “Tools” level, analysts are taking away one or more specific tools that an adversary would use in an attack. At the apex of the pyramid are the TTPs (Tactics,Techniques and Procedures), when analysts detect and respond at this level, they are operating directly on the adversary’s behaviors, not against their tools, forcing them to learn new behaviors.
There are three types of hunts.
- Intelligence-Driven (Atomic Indicators) – These are low-hanging fruit hunts. They are generally known threats that bypass traditional security controls
- TTP-Driven (Behavioral and Compound Indicators) – These are hunts looking for techniques used by advanced attackers, where analysts take a methodological approach for discovering unknowns. Generally attempting to interrupt the adversaries TTPs (Techniques, Tactics, and Procedures)
- Anomaly-Driven (Generic Behaviors) – These hunts are based on low-prevalence artifacts and outlier behaviors. These are unknown threat leads.
Benefits of Starting a Threat Hunting Practice
There are many benefits from starting a threat hunting practice. Obviously, discovering and thwarting an attack before it causes significant damage. However, what about a threat hunt that doesn’t find anything? Is that really a bad thing? Having stronger knowledge of vulnerabilities and risks on the network will allow a hardening of your security environment which in turn should equate to fewer breaches and breach attempts. Moreover, the insights gathered from threat hunts will aid in reducing the attack surface. Another key result from beginning a threat hunting practice is that security teams will realize increased speed and accuracy of threat responses. Ultimately, organizations should witness measurable improvements for key security indicators such as mean time to detect and mean time to respond.
In-House or Outsourced?
Through outsourcing, threat hunting can be accessible for organizations of all sizes, but especially for small and medium sized organization as they often do not have a Security Operations Center (SOC) as it often is too expensive to build and support. Many Mid-Market sized companies have a SOC and are considering the addition of threat hunting to their current environment. Enterprise and large organizations perhaps are looking for assurance by augmenting existing threat hunting efforts. And in many cases, these enterprise organizations simply want to empower and educate their staff.
***Just in time for RSAC, Cisco is pleased to announce that it will be adding Threat Hunting as a feature to our Cisco AMP for Endpoints offering. Our new threat hunting by Cisco Talos uniquely identifies advanced threats, alerting our customers before they can cause any further damage by:
- Uncovering hidden threats faster across the attack surface using MITRE ATT&CK
 and other industry best practices
and other industry best practices - Performing human-driven hunts based on playbooks producing high fidelity alerts
- Continually developing systematic playbooks, executing on broad, low-level telemetry on product backend
Our new threat hunting capability:
- Is provided by Cisco Talos, the largest non-governmental threat intelligence organization on the planet
- Is not limited to just one control point (i.e.: endpoint), instead, we hunt across multiple environments
- Uniquely combines our new Orbital Advanced Search technology with expertise from elite threat hunters to proactively find more sophisticated threats
If you are at RSAC be sure to stop by our booth #6045 in the North Hall. If you aren’t at RSAC, sign up for a Cisco Threat Hunting Workshop to learn more about Threat Hunting.
The post Threat hunting doesn’t have to be difficult—Taking a proactive position with your cybersecurity appeared first on Cisco Blogs.

