Remote work and the threat landscape
May 28, 2020
The New Era of Business Continuity – What does it mean today?
May 28, 2020Cisco is Building a Bridge to Secure Access Service Edge
By Jeff Reed, SVP of Product, Security Business Group
In partnership with Scott Harrell, SVP/GM of Cisco Intent-Based Networking Group
As leaders of Cisco’s Networking and Security organizations
for the last eight years, Scott Harrell and I have had the opportunity to oversee
many innovative developments from our dual perspectives. In fact, each of us has
had the other’s role, which provides us with unique views into the future of
secure networking. Recently we had the opportunity to rethink how networks and
security will become even more intricately intertwined as organizations change
the way they connect their distributed workforce to applications and data resources.
The main macro-trend we considered is the transition to multi-cloud, resulting in data and applications that are literally located everywhere. In parallel, an increasingly distributed workforce requires secure access to applications with optimal performance. The rapid adoption of SD-WAN for connecting to multi-cloud applications provides enterprises with the opportunity to rethink how access and security are managed from campus to cloud to edge. With 60% of organizations expecting the majority of applications to be in the cloud by 2021 and over 50% of the workforce to be operating remotely, new networking and security models, such as Gartner’s Secure Access Service Edge (SASE), provide a vision for managing the new normal.
The Journey to SASE
Gartner’s concept of Secure Access Service Edge provides the ability to identify end users, devices, IoT/OT systems, and edge computing locations and provide direct and secure access to applications hosted anywhere, including data centers and cloud-based services. Specifically, Gartner says that SASE “…is an emerging offering combining comprehensive WAN capabilities with comprehensive network security functions (such as SWG, CASB, FWaaS and ZTNA) to support the dynamic secure access needs of digital enterprises.”*
The goal of SASE is to provide secure access to applications
and data from your data center or cloud platforms like Azure, AWS, Google Cloud,
and SaaS providers based on identities—specific individuals, groups of
people at certain office locations, devices, IoT, even services. Service
edge refers to global point of presence (PoP), IaaS, or colocation facilities
where local traffic from branches and endpoints is secured and forwarded to the
appropriate destination without first traveling to data center focal points. By
delivering security and networking services together from the cloud, organizations
will be able to securely connect any user or device to any application with the
best experience.
Gartner considers SASE to be a vision of a future
secure networking model for enterprises to strive for—it’s not currently a
reality from any vendor. Cisco has been moving down this path for several years
through key acquisitions in networking (Meraki, Viptela) and security (OpenDNS,
CloudLock, Duo) as well as many internally developed innovations. Today, SASE
is best represented by the convergence of cloud-managed SD-WAN and cloud-delivered
security, two foundational capabilities that Cisco has developed extensively.
Today, more than 20,000 organizations have begun the journey
to SASE by deploying Cisco SD-WAN and more than 22,000 have deployed Cisco Umbrella’s
cloud security services.
Challenges to Realizing SASE
Moving to a SASE model will be a gradual process as
enterprise IT rethinks how to connect a remote workforce to the distributed
information resources they need. Flexibility will be fundamental as IT chooses
among multiple security and networking capabilities that best fit their
operations, regulatory requirements, and types of applications. Security
services can be predominately delivered from the cloud to provide consistent
access policies across all types of endpoints. However, globally-distributed
organizations may need to apply security and routing services differently
according to regional requirements.
Beyond the architectural choices that enterprises will need to make, IT needs to consider how to streamline procurement of security and networking services. Today these technologies typically have separate buying cycles, which may slow SASE adoption. Secondly, licensing structures are different for networking, which are typically throughput-based, versus security services, which are based on protecting a wide variety ofusers and endpoints. As IT strives to move from on-premise towards a hybrid or cloud-first approach, there will be an increasing demand for “as-a-service” consumption models that offer more flexibility for procurement.
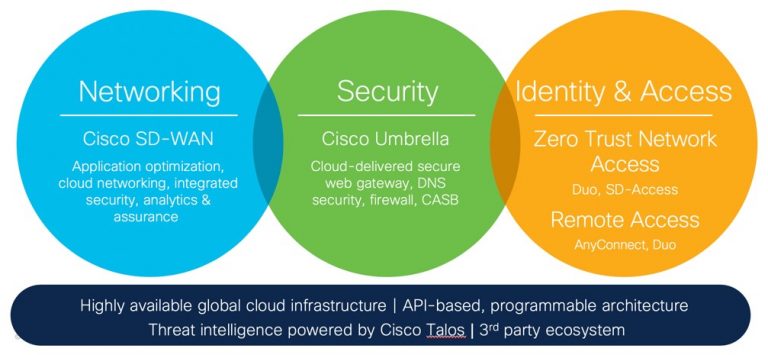
Between Networking, Security, and Zero Trust Network Access, Cisco is Building a Bridge
Cisco has many of the SASE capabilities already in place, with additional integration among current solution sets well underway.

Networking: Cisco SD-WAN is a cloud-delivered overlay WAN architecture with application optimization to deliver predictable application performance in multi-cloud environments. A full security stack is built in, and offers firewall, IPS/IDS, AMP and URL Filtering. Analytics and Assurance deliver the visibility and insights over any type of connectivity to deliver the best experience.
Cloud Security: Cisco Umbrella unifies secure web gateway (SWG), DNS-layer security, firewall, and cloud access security broker (CASB) functionality in one a single integrated cloud-native platform. Built as a micro-services-based architecture with dozens of points of presence around the world, Umbrella provides the scale and reliability needed to secure today’s remote workforce. Powered by threat intelligence from Cisco Talos, the largest non-governmental threat research team in the world, Umbrella was recently ranked #1 in the industry for security efficacy.
Zero Trust Network Access: To verify identity and protect access to resources, Cisco’s Duo and Software-Defined Access (SD-Access) enable a zero trust network access architecture to be extended anywhere people work. Duo provides protection for your workforce, while SD-Access protects your workplace. Ultimately, IT is less concerned about where the security functions are implemented and can focus more on the policies that they need to enable throughout the enterprise.
Foundational capabilities of this SASE model include an API-based, programmable architecture that provides flexibility to encompass many types of enterprise use cases, including support for third-party ecosystem partners.
Crossing the Bridge to SASE
Moving to a SASE model will be a gradual process as enterprise IT rethinks how to connect a remote workforce to the distributed information resources they need. Flexibility will be fundamental as IT chooses among multiple security and networking capabilities to best fit their operations, regulatory requirements, and types of applications. The bridge that enterprises choose to evolve their infrastructure to a SASE model should be structured on a cloud-native, micro-services architecture. Achieving the benefits of SASE will be more difficult to achieve if existing on-premises technology is merely shifted to virtual machines running as cloud services. Cloud security and networking services will only become more critical as enterprises cross the bridge to employ Secure Access Service Edge networking to solve disruptive information management challenges.
To learn more about how Cisco is enabling organizations to build a bridge to the SASE networking and security model, you’ll want to attend Cisco Live! June 2 – 3, 2020. To date, there are already over 80,000 registered attendees for Cisco Live! You won’t want to miss this virtual event from the comfort of your office. Register today at https://www.ciscolive.com/us.html.
*Source: Gartner, The Future of Network Security Is in the Cloud, Neil MacDonald, Lawrence Orans, et al., 30 August 2019.
The post Cisco is Building a Bridge to Secure Access Service Edge appeared first on Cisco Blogs.

