
Malaysian conglomerate promotes a collaborative culture with Office 365
May 28, 2020
Cisco is Building a Bridge to Secure Access Service Edge
May 28, 2020Remote work and the threat landscape
Last month, after the dust had settled from the move from office to remote work, we took a look at ways you could improve your security posture. In it, we discussed how you can shore up older and personal devices now being used for work tasks, how to reduce your security footprint with company-sanctioned software, and ways to ensure that connections back into the company network are secure.
This month, we decided to take a look at some of the trends we’ve seen in a shifting threat landscape, including attackers who are adapting their techniques to take advantage of new opportunities. When you understand what they’re doing, it’s easier to mount a better defense against new trends in the threat landscape.
The great migration
Before diving into what attackers are up to, let’s take a look at just how significant the shift to remote work has been. To do this, we took a look at traffic running through Cisco Umbrella’s DNS servers to see where it was coming from, giving us a snapshot of internet activity. In particular, we looked at distinct IP addresses, sorting them into remote and office groupings. The following chart shows the trend for the total number of IP addresses known to be remote each week.

In mid-March, we can see a marked increase in remote connections. While it’s interesting to note an inverse correlation between office-based connections to Umbrella (declining) and remote connections (increasing), even more interesting is by how much remote connections increased.
Comparing the first and last weeks of March, the number of remote workers had effectively doubled. This means that IT teams have been dealing with setting up a lot of remote workers. This can potentially spread resources thin and, given the number of new remote connections, requires attention to look out for threats in this expanded environment. (Note: new Umbrella customers who have recently signed up to our Umbrella trial have been filtered out in the above chart.)
A topical shift in spam
It’s not news that spammers leverage the latest big stories in their emails in order to help spread their wares. The pandemic has been no exception. As reported by Talos on a number of occasions, threat actors have used it in a wide variety of malicious campaigns.
Some campaigns have sent out malicious emails that appear to share government information on the pandemic, while others claim to contain information regarding government stimulus payments. This shift to pandemic-related campaigns is so pronounced that malicious spam campaigns focusing on package delivery have pivoted to claim that deliveries have been postponed due to the pandemic:

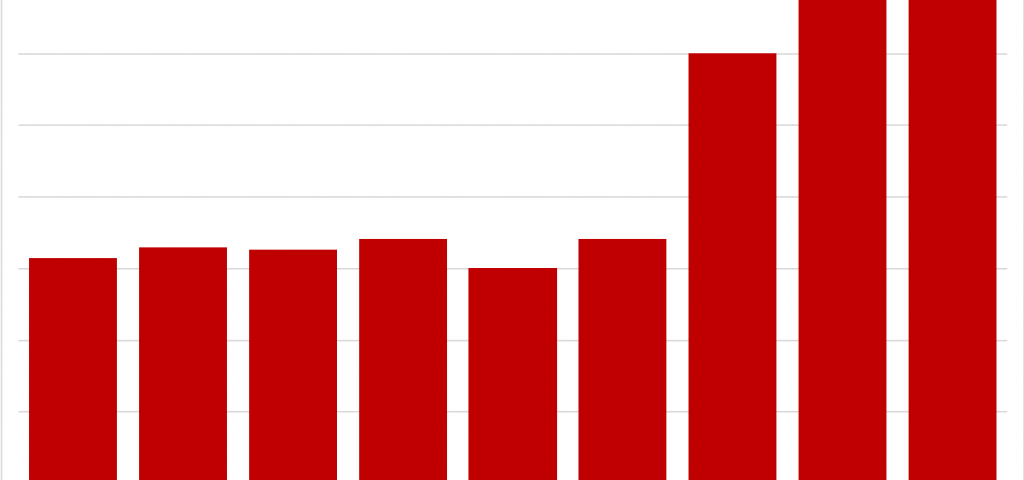
What’s interesting is not just the variety of email scams and tricks being peddled on the threat landscape, but the volume of pandemic-related spam campaigns. To determine just how much spam contained pandemic-based themes, Talos looked at distinct emails sent out that contained the terms “pandemic,” “COVID-19,” and “corona.”

While emails containing these key words first began to grow in early February, there is a clear increase in mid-March, when the pandemic was constantly in the headlines and coinciding with the migration to remote work discussed above. At its peak, more than 20 percent of all email observed by Talos referenced the pandemic. (Note: the regular dips in the chart coincide with weekends. It’s also worth noting that a portion of ham or marketing emails were also mentioning the pandemic during this time.)
Malicious domains
In early April, researchers from Umbrella took a look at the increase in malicious domains that bad actors were leveraging to carry out attacks. According to Umbrella researchers, on March 19th, enterprise customers connected to 47,059 domains that contain “covid” or “corona” in the name. Of these, four percent were blocked as malicious.
We decided to revisit this data to see what has happened two months later. By May 19th, this number had increased to 71,286 domains, where 34 percent of them were blocked as malicious.

Despite this being a marked increase from March, late April appears to be the point where the most malicious activity took place. During this time the percentage of domains blocked as malicious frequently crossed 50 percent, even peaking as high as 75 percent. While this declined in early May, the percentage of malicious domains regularly sat between 30-40 percent in mid- to late-May.
Protect against the trends
Overall, bad actors have upped their activity with pandemic–related themes surrounding malicious spam and domains. The good news is that the systems required to protect your organization from these security risks haven’t shifted much.
For starters, Cisco Umbrella’s cloud-based services can protect users from malicious internet destinations. The malicious domains that have been registered in the last few months are all flagged as malicious within Umbrella’s DNS infrastructure, preventing users with your organizations from connecting to them and becoming compromised.
Similarly, Cisco Email Security is well equipped to identify and filter the influx of pandemic–related spam aimed at your user’s inboxes. The advanced phishing protections and machine learning capabilities within can quickly identify these malicious spam campaigns, not just by the topic, but by understanding and authenticating email identities and behavioral relationships, filtering out spam emails and prevent attacks.
Also, we discussed last month, Cisco has expanded and extended trial offerings on a number of security products. Umbrella has one such offering, as does AMP for Endpoints, which can be used to secure the additional remote desktops now on the company network. AMP can help you gain visibility and control of remote devices, allowing you to see where a threat came from, where it’s been, what it’s doing, and if necessary, isolate compromised endpoints.
Finally, to secure that remote connection back into the company network, consider using Cisco AnyConnect Secure Mobility Client with Duo Security. AnyConnect can simplify secure access to the company network, while Duo can ensure that the person logging into your network is who they say they are.
Free and expanded offerings for Umbrella, AMP, AnyConnect, and Duo are all available through our Cisco Secure Remote Worker page.
Enjoyed reading this Threat of the Month? Subscribe to the Threat of the Month blog series and get alerted when new blogs are published.
The post Remote work and the threat landscape appeared first on Cisco Blogs.

