Why I Joined Cisco Security and Its Culture of Innovation and Inclusion
July 30, 2021
Introducing our new CISO Advisor, Pam Lindemeon
August 3, 2021Detect What Others Miss with CESA
With the executive order signed by the US government in the wake of recent cybersecurity attacks like SolarWinds, Colonial Pipeline, Microsoft Exchange server breach that have plagued high-value government entities and private organizations, it is very important to have security ammunition ready that can detect such attacks – one that can provide deep forensic details and visibility into your users and endpoints.
In the SolarWinds breach, a form of supply chain attack, the attacker spent months performing undetected reconnaissance to gain deep understanding of the inner workings of the trusted IT supplier before targeting them as the means to infiltrate US government targets bypassing ransomware defense in endpoint anti-malware solutions. The attack went undetected by many security solutions for months. New supply chain attacks are happening regularly, with many of them targeting endpoint security components directly and with many more such new techniques emerging, it is more important than ever to have a defense-in-depth endpoint strategy with forensics capabilities.
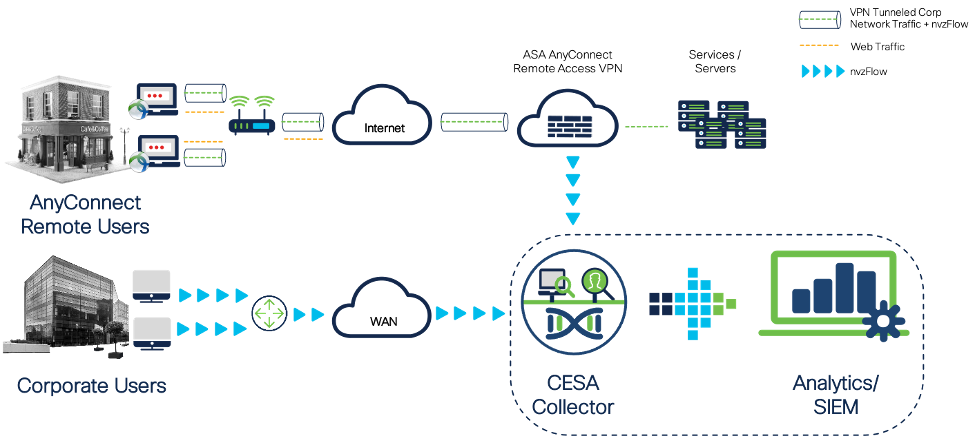
Cisco Endpoint Security Analytics (CESA) helps solve this problem and can be that security ammunition in your security infrastructure to act as an early threat warning system by providing behavior-based deep – user, endpoint and network visibility all in one place. The three components that forms the overall CESA solution are
- Cisco’s AnyConnect Network Visibility Module (NVM) that provides unparalleled endpoint behavioural visibility
- CESA Collector that acts as an NVM telemetry broker, converting IPFIX NVM data into SIEM consumable Syslogs
- Analytics platform like Splunk that can transform the endpoint telemetry data into meaningful insights and alerts

With the latest CESA 3.1.11 release, we have added the following features that makes it even more secure as well as provide newer user and endpoint telemetry to help you detect advanced forms of attacks.
SecureX Integration
You can now unleash the full power of SecureX threat response and accelerate the time-to-value, through the SecureX CESA Relay module (Figure 2). Through the CESA module, you can perform threat investigations using sightings of observables from CESA and use SecureX for remediation and response actions as shown in Figure 3. For example, if Umbrella had categorized a certain domain with neutral reputation, through CESA, if you observe that the process which originated the traffic to this destination domain has never connected earlier, and hence indicates a malicious activity; you can now view this relationship in SecureX, through the SecureX CESA Relay module. You can then take a response action to block the domain immediately with Umbrella and other security controls in your network.


Secure NVM Transport
With the introduction of DTLS 1.2 support in NVM, all communications between the client and the CESA collector is now encrypted and secured. Prior to this release the information was sent over plain text UDP which could be susceptible to Man-in-the-Middle (MITM) attack where an attacker had visibility into all NVM traffic between the client and the collector. With the secure DTLS connectivity to the collector, the NVM client first verifies the availability of the collector before sending the telemetry data over the encrypted channel thus preventing network sniffing, spoofing, reconnaissance and MITM type of attacks.

Trace Path of Malicious Software
CESA can now alert you when an application is being executed from illegitimate or unexpected paths by tracing such suspicious/malicious activity all the way down to the process path of the known, unknown, or modified executable. This helps in Zero-day analysis of attacks based on suspicious activity thus simplifying your investigations. With the new Process Path Investigation dashboard, you can now see the process path from where the process was executed. In the Figure 5 below you can see that that the process “svchost.exe” is being executed from a suspicions path “d1ecfbd***”.

Find Ultra-Stealthy Threats
CESA can now also provide additional visibility into process command line arguments helping you detect attack methods such as obfuscation or other malicious evasion techniques. You can now detect unusual command line arguments to exploitable executables (eg., /bin/sh, powershell.exe, wmic etc), files given as arguments to other programs as well as whole malicious script in obfuscated form being sent as command line argument to run. With the new Process Path Investigation dashboard, you can see in Figure 6 that an attacker who has compromised the root user is trying to ssh into 10.126.111.235.

Logged-in User Visibility
Prior to this release, CESA reported console user as the originator of all traffic for all user processes. An attacker could SSH into a compromised endpoint and start performing malicious activity hiding his tracks behind that of the console user of the endpoint. With the new release, CESA reports logged-in user for remote sessions like RDP and SSH for processes launched through such sessions. As you can see below, the user “Raghul” is initiating a “Data hoarding” activity by having remotely logged into the DESKTOP-ONFHG3.

Learn more about CESA and how it can protect your network and endpoints.

