Now you can bring family and friends together to call, chat, and make plans – all in one app with Microsoft Teams
May 18, 2021Extending Detection into Automated Response with SecureX and Secure Cloud Analytics
May 19, 2021New Study: Reducing Security Incidents and Impact with Endpoint Protection
The way we work has fundamentally changed since the beginning of last year. We are now part of a new, massively remote workforce that is here to stay. Organizations have long struggled with maintaining visibility across an increasingly complex attack surface. Now, with more employees relying on access to resources and applications from outside the office, endpoint protection has become crucial to the success of any cybersecurity program. But finding success in cybersecurity doesn’t come easy, especially in such a fragmented market with thousands of solutions and vendors to choose from.
So, what if you could gauge how the capabilities of a security solution would contribute to achieving said success? What if you could measure the impact of deploying a specific tool to determine whether it can simplify complexity, minimize your attack surface, and accelerate threat response? This week at the RSA Conference, we’re unveiling our new Security Outcomes Study: Proven Success Factors for Endpoint Security, which does just that.
We examined the responses of over 4,800 IT and security professionals from 25 countries to determine how an endpoint security solution equips them to build more successful cybersecurity programs, while battling today’s top threats. Through this extensive analysis, we can objectively say that endpoint security plays a vital role not only in avoiding major incidents but also enabling the business.
Trends in Reported Incidents
Knowing how our peers defend against, or respond to, security incidents can tell us a lot about how to effectively navigate the current threat landscape. One of the key areas we examined closely was the major incidents and losses reported by 41% of the 4,800 respondents. For organizations reporting a major incident, we then dug deep into the most common types of incidents they’d experienced over the last two years.
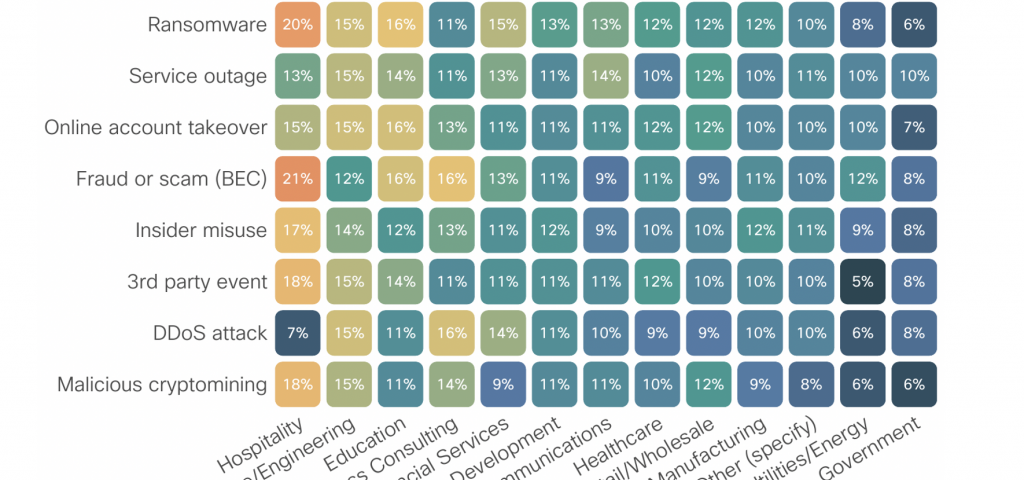
For purposes of brevity, we didn’t get into too much detail in the actual report, but I wanted to relay some additional insights for you here. We noticed that the reported incident rates accurately represent the study’s global scope – with incidents varying significantly across regions and industries. Specifically, through this comparison, we found that certain verticals reported considerably more incidents than others.
The top five industries reporting a major security incident included the hospitality, architecture/engineering, education, business consulting, and financial services sectors. These industries experienced higher incident rates across the board, with hospitality companies falling victim to more data breaches (23%), fraud or scams (21%), and ransomware attacks (20%) than other industries. On the opposite side of the spectrum was the energy and public sectors, reporting far fewer incidents across all types of security threats.

In addition to examining incident types by sector, we were also curious about differences based on organization size. We found it rather surprising to learn that the overall rate of major security incidents in small businesses (35%) didn’t differ substantially from that of large enterprises (37%). In fact, organizations falling in between these firm sizes appeared to be the most susceptible to security incidents.
Organizations ranging from 500 to 1,000 employees report the highest likelihood of significant cyber events.
What’s more, this general trend remains fairly consistent across the incident categories shown in Figure 2 below. It’s possible that companies in this size range are too big to fall below attackers’ radars, yet not big enough to leverage enterprise-level resources for defense. The “growing pains” of building a cybersecurity program, perhaps?
We also asked respondents reporting major security incidents about the impacts associated with those events. Operational impacts were by far the most common overall, which makes sense because major events force people (and systems) to stop their normal business activities in response to the incident. Organizations also commonly cited direct financial losses in the wake of major incidents.

Regulatory action lands next in overall frequency and serves as a reminder that the consequences of security incidents go beyond the direct costs to the victim organization. Secondary or indirect impacts are a big deal. To that point, brand damage, business relationships, lost revenue, and legal action are all on the list. The fact that cyber events are fraught with externalities means that secondary stakeholders (like regulators, business partners, and customers) will take actions that impact the organization after an incident.
Finally, it makes sense that different types of incidents would result in different types of losses, and Figure 3 below tests that theory. As you digest it, keep in mind that we did not ask about impacts specific to each type of incident; respondents selected impacts experienced over the last two years across all incidents.
Think of Figure 3 as more of a correlation matrix rather than a causal analysis. In other words, 32% of organizations that reported data breaches also reported operational impacts (top left), but we don’t know for sure if those operational impacts resulted from the breach or some other type of incident in the two-year timeframe.

One in three (32%) of organizations that reported a data breach also reported experiencing operational impacts.
How Cisco Secure Endpoint Can Help
This recent history of incidents experienced by real organizations helps us paint a picture of what we should be focusing on to better manage risk. As mentioned, our study found that a robust endpoint security solution is essential for not only avoiding such incidents (and their potential impacts) but also the overall effectiveness of cybersecurity programs.
Our analysis concluded that Cisco Secure Endpoint contributes to every single objective examined in the Security Outcomes Study. From enabling accurate threat detection and timely incident response to leveraging performance metrics and deploying a well-integrated security solution, together these proven practices are the puzzle pieces to maximizing cybersecurity success.
Download your copy of the Security Outcomes Study: Proven Success Factors for Endpoint Security, and you’ll be on your way to enabling a remote workforce, all while achieving a reduced attack surface, faster remediation, and improved security operations.
LEARN MORE ABOUT CISCO SECURE ENDPOINT
We’d love to hear what you think. Ask a Question, Comment Below, and Stay Connected with Cisco Secure on social!
Cisco Secure Social Channels
Instagram
Facebook
Twitter
LinkedIn

